CYBERINC NOW PART OF FORCEPOINT
Learn More About RBI
Together We're Making RBI Smarter.
Now you can safely fetch, execute, and render content with context-aware isolation.
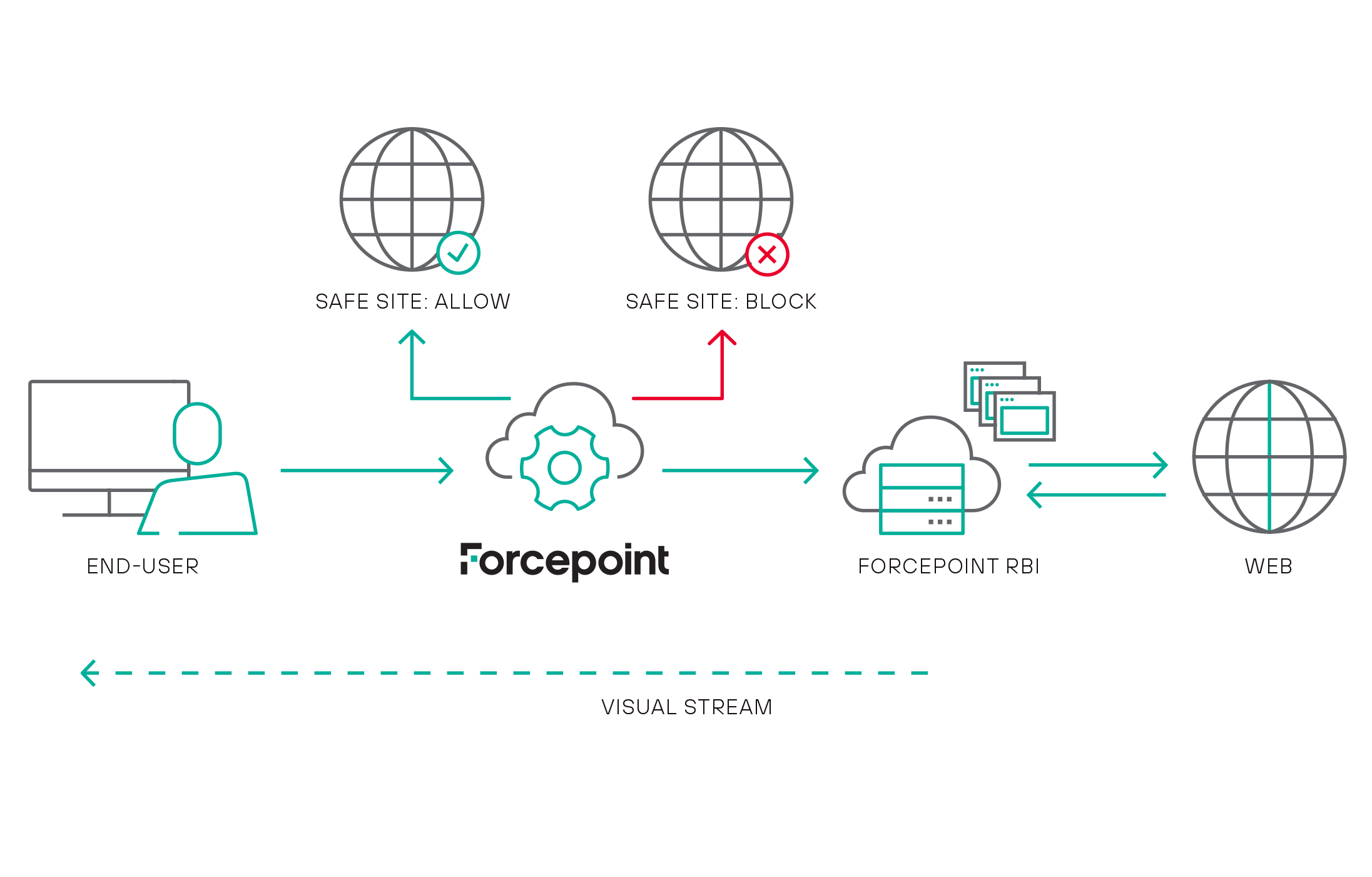
Taking Remote Browser Isolation (RBI) to the next level in SASE
The Forcepoint Data-first SASE platform enables enterprises to use the cloud to transform their network and security architectures. It goes beyond simply protecting access to resources; by putting data security first. Read Jim Fulton’s blog on how Cyberinc’s Remote Browser Isolation has become a key component utilized within Forcepoint’s Data-first SASE architecture.
Read BlogExplore Forcepoint Remote Browser Isolation
Protect endpoints and networks from web threats and phishing attacks with Forcepoint Web Security with Remote Browser Isolation
Learn More About RBI